The Facebook names of some Nigerian scammers have been exposed on a US blog, and the boys ain't even know it. Lol. US security blog Krebsonsecurity.com, published links to the real Facebook profiles of Nigerians allegedly involved in 'Yahoo' business....and if you check their profiles, the guys are balling, pictures taken with jewelries, exotic cars etc...from Nigeria to Turkey to Malaysia! But the funniest part of all this is that these boys don't even know that their names have been exposed. See the report from Krebs on Security below...
The article below written by the blogger at Krebsonsecurity.com
Earlier this week, I wrote about an online data theft service that got hacked. That compromise exposed a user base of mostly young Nigerian men apparently engaged in an array of cybercrime activities — from online dating scams to 419 schemes. It turned out that many of these guys signed up for the data theft service using the same email address they used to register their Facebook accounts. Today’s post looks at the social networks between and among these individuals.
Of the nearly 3,000 BestRecovery users, about 280 of them had Facebook accounts tied to their BestRecovery email addresses. George Mason University associate professor Damon McCoy and several of his grad students volunteered to scrape those profiles that were open and map their social networks to see if there were any obvious or discernible patterns in the data.
The raw data itself — which ranked the BestRecovery users on number of connections they had to other users — was potentially useful, but difficult to parse into meaningful chunks. Oddly enough, as
I was poring over that data I heard from Chris Ahlberg, the CEO of Recorded Future Inc., a Cambridge, Mass. software company that specializes in Web intelligence and predictive analytics. Ahlberg was writing to say that he enjoyed the blog — particularly the posts with data-intensive analyses — and that he’d be delighted to collaborate on a data-rich research project at some point. I told him his timing couldn’t have been more serendipitous.
Ahlberg and his team took the raw scraped data sets from the Facebook accounts and ran it through their cyber intelligence applications. In short order, they produced some very compelling and beautiful graphs, shown below.
Staffan Truvé, Recorded Future’s chief technology officer noted that — with few exceptions — the BestRecovery users largely appear to belong to one of two very separate social networks.
“There appears to be two fairly separate, quite tightly knit networks, each with a few central leaders, and also with just a few individuals being the bridge between the two networks — and that those middlemen are themselves not connected,” said Staffan Truvé, Recorded Future’s chief technology officer.
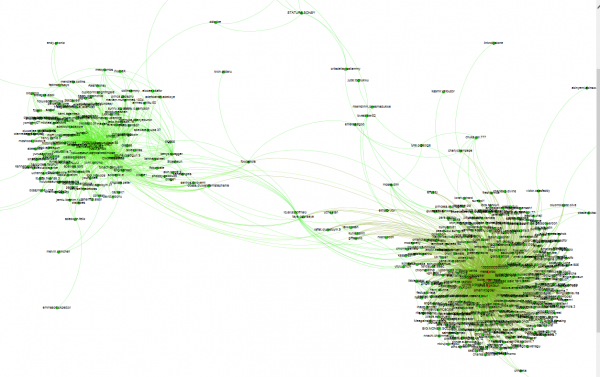
I noted in my previous story that a majority of the BestRecovery keylog service users who had Facebook pages that reported a location listed either somewhere in Nigeria (usually Lagos), or Kuala Lumpur, Malaysia. Not surprisingly, those two geographic groups are generally represented by these two globs of Facebook users (with several exceptions of users who are from Nigeria but living in Kuala Lumpur and vice versa).
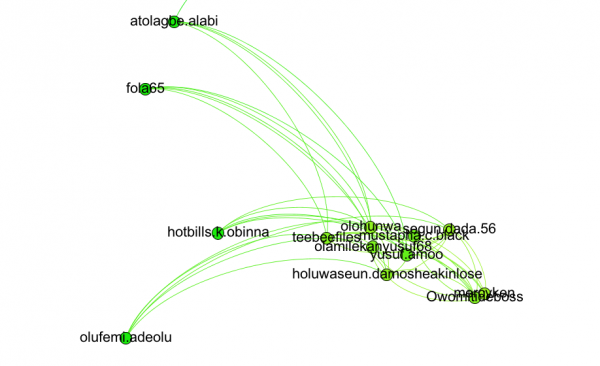
Here’s a closer look at the most influential/connected members at the center of Cluster 1 (upper in the diagram above)
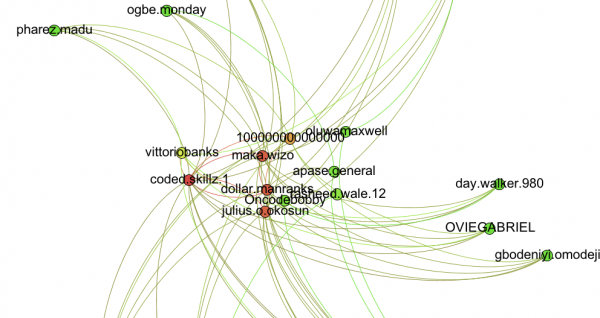
Now, let’s have a look at the big men from Cluster 2 (bottom right in the first image in this blog post). Red yellow and red indicate a higher number of contacts within this group:
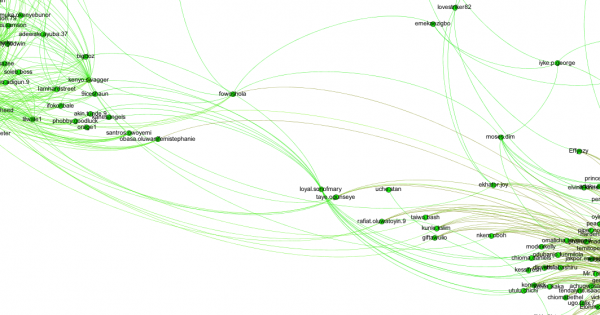
Here’s a closeup of the handful of middlemen who bridge these two social clusters:
The Facebook profiles of most of the top guys in those clusters can be be seen in this photo montage that I put together for the previous post in this series.
By the way, if anyone is interested in the email addresses used by these Facebook profiles and customers of the BestRecovery keylogger service, they’re available here.
The video below...
A crude but effective online service that lets users deploy keystroke logging malware and then view the stolen data remotely was hacked recently. The information leaked from that service has revealed a network of several thousand Nigerian email scammers and offers a fascinating glimpse into an entire underground economy that is seldom explored.
The site was so poorly locked down that it also exposed the keylog records that customers kept on the service. Logs were indexed and archived each month, and most customers used the service to keep tabs on multiple computers in several countries. A closer look at the logs revealed that a huge number of the users appear to be Nigerian 419 scammers using computers with Internet addresses in Nigeria.It's a pretty long write up, so read it after the cut. The video showing the alleged 'Yahoo Boys' is also after the cut....
The article below written by the blogger at Krebsonsecurity.com
Earlier this week, I wrote about an online data theft service that got hacked. That compromise exposed a user base of mostly young Nigerian men apparently engaged in an array of cybercrime activities — from online dating scams to 419 schemes. It turned out that many of these guys signed up for the data theft service using the same email address they used to register their Facebook accounts. Today’s post looks at the social networks between and among these individuals.
Of the nearly 3,000 BestRecovery users, about 280 of them had Facebook accounts tied to their BestRecovery email addresses. George Mason University associate professor Damon McCoy and several of his grad students volunteered to scrape those profiles that were open and map their social networks to see if there were any obvious or discernible patterns in the data.
The raw data itself — which ranked the BestRecovery users on number of connections they had to other users — was potentially useful, but difficult to parse into meaningful chunks. Oddly enough, as
I was poring over that data I heard from Chris Ahlberg, the CEO of Recorded Future Inc., a Cambridge, Mass. software company that specializes in Web intelligence and predictive analytics. Ahlberg was writing to say that he enjoyed the blog — particularly the posts with data-intensive analyses — and that he’d be delighted to collaborate on a data-rich research project at some point. I told him his timing couldn’t have been more serendipitous.
Ahlberg and his team took the raw scraped data sets from the Facebook accounts and ran it through their cyber intelligence applications. In short order, they produced some very compelling and beautiful graphs, shown below.
Staffan Truvé, Recorded Future’s chief technology officer noted that — with few exceptions — the BestRecovery users largely appear to belong to one of two very separate social networks.
“There appears to be two fairly separate, quite tightly knit networks, each with a few central leaders, and also with just a few individuals being the bridge between the two networks — and that those middlemen are themselves not connected,” said Staffan Truvé, Recorded Future’s chief technology officer.
I noted in my previous story that a majority of the BestRecovery keylog service users who had Facebook pages that reported a location listed either somewhere in Nigeria (usually Lagos), or Kuala Lumpur, Malaysia. Not surprisingly, those two geographic groups are generally represented by these two globs of Facebook users (with several exceptions of users who are from Nigeria but living in Kuala Lumpur and vice versa).
Here’s a closer look at the most influential/connected members at the center of Cluster 1 (upper in the diagram above)

Now, let’s have a look at the big men from Cluster 2 (bottom right in the first image in this blog post). Red yellow and red indicate a higher number of contacts within this group:

Here’s a closeup of the handful of middlemen who bridge these two social clusters:

The Facebook profiles of most of the top guys in those clusters can be be seen in this photo montage that I put together for the previous post in this series.
By the way, if anyone is interested in the email addresses used by these Facebook profiles and customers of the BestRecovery keylogger service, they’re available here.



No comments:
Post a Comment